wiz discovered ,Defenders in cybersecurity have long struggled to stay ahead of attacks hitting the software development life cycle, or SDLC.
Over the past year, we’ve seen a wave of incidents in which hackers targeted the very tools and systems used to build software, including the Ultralytics hijack, the Shai-Hulud campaigns, and the Trust Wallet breach.
These attacks show a clear shift: criminals aren’t just hunting bugs in finished code anymore.
They’re going after the factories and the infrastructure that creates it. While we have solid guides like MITRE ATT&CK for protecting computers and cloud setups, SDLC systems have been left to patchwork defenses.
That’s where the new SDLC Infrastructure Threat Framework, or SITF, steps in. It’s an open tool built to help teams map and stop these threats.
What Makes SITF Different
SITF focuses on the five main parts of SDLC infrastructure: your local coding setup (IDEs and endpoints), version control systems such as GitHub, continuous integration and deployment pipelines (CI/CD), package registries like npm or PyPI, and even production environments.

It lists more than 70 attack methods specific to these areas. Think of things like fake commits slipping into your repo or poisoning the cache in your build pipelines.
What sets it apart is a simple three-part breakdown for every threat. First, the technique the attacker uses, such as submitting a bad pull request from a forked repo.
Second, the risk of why it worked, such as allowing those pull requests to run workflows that touch secrets. Third, the fix practical steps like setting branch protection rules or requiring manual approval for forks.
This chain helps you trace back from spotting an attack to plugging the real hole.
Then there’s the Attack Flow Visualizer. It’s a drag-and-drop tool for sketching how an attack jumps from one system to another.
No more guessing at isolated problems. You start with an entry like a phishing email and draw lines to the endgame, as a follow-on supply chain hit.
It even spits out a ready-made list of defenses, sorted by attack stage and system part, so you focus on stopping things early.
Breaking Down the Shai-Hulud 2.0 Attack
To show how it works, let’s walk through Shai-Hulud 2.0, one of the craftiest supply chain worms yet.
This thing spread like wildfire, hitting thousands of open-source repos on GitHub and npm. It wasn’t a one-off hack; it chained nine steps across VCS, CI/CD, registries, and developer machines.
It kicked off with a malicious pull request from a fork, labeled T-C003 or PWN Request in SITF. The repo lets forks trigger CI/CD workflows, and those workflows have access to secrets like npm publish tokens.
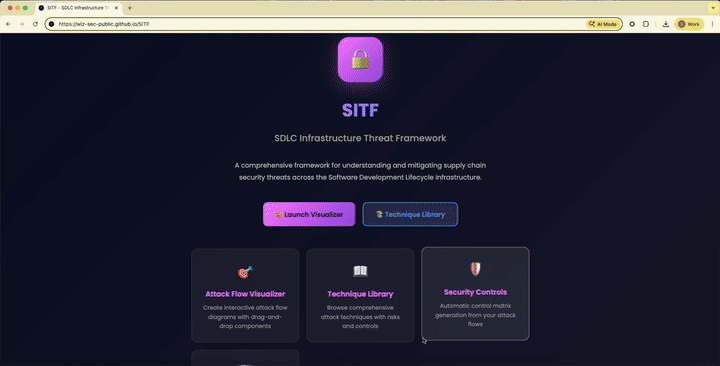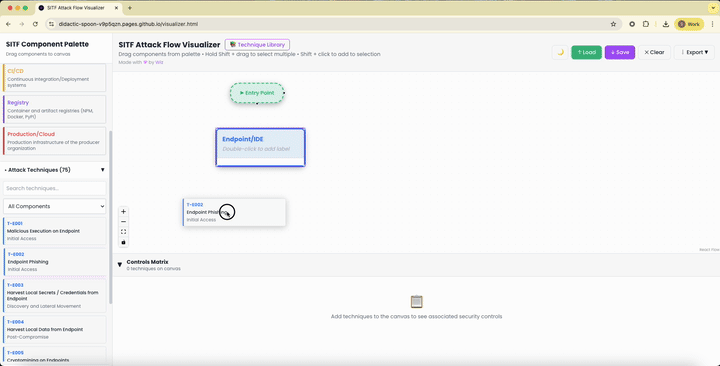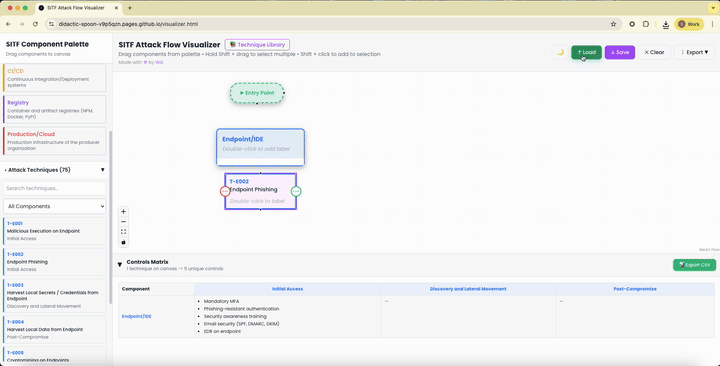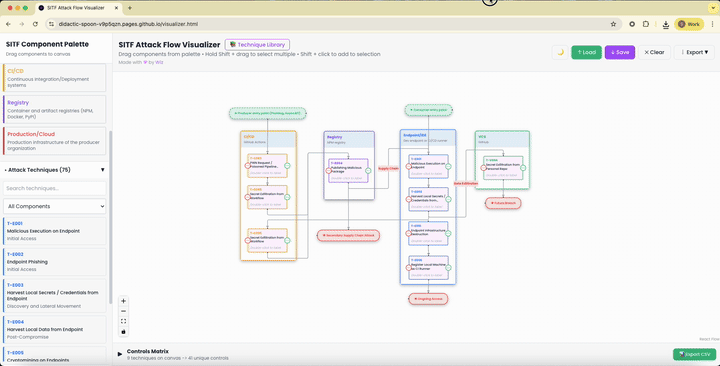
That was the open door. From there, step two dumped those secrets using a sneaky build script. Step three pushed out tainted packages to the public registry.
Next came the pivot to endpoints. Developers and build runners grabbed the bad packages, running malware right on their laptops.
The code then scanned for credentials with tools like TruffleHog, exfiltrated additional secrets via fake workflows, and even attempted to sign up the infected machine as a self-hosted CI runner for persistence.
If that failed, it wiped files or uploaded stolen data to a personal repo. SITF’s visualizer lays this out clearly, highlighting fixes like endpoint detection tools, signed browser extensions, and trusted publishing rules.
| System | Attack Stage | Key Defense |
|---|---|---|
| Endpoint/IDE | Initial Access | Install EDR software |
| Endpoint/IDE | Initial Access | Only use signed extensions |
| VCS | Movement Around | Ban personal repos for work |
| VCS | Movement Around | Watch audit logs closely |
| CI/CD | Initial Access | Enforce branch protections |
| Registry | Movement Around | Require trusted publishers |
Real-World Lessons from Past Breaches
These aren’t just theories. Look at Ultralytics in late 2024. Hackers sent pull requests with malicious shell commands hidden in branch names.
They exploited a trigger called pull_request_target, injecting cryptominers into popular YOLO AI models via functions such as safe_run. Users noticed CPU spikes, but not before it spread via PyPI.
A quick rollback to version 8.3.43 limited damage, but it exposed how IDE and CI tweaks can cascade.
Trust Wallet faced a similar nightmare in 2025, linked to Shai-Hulud. Attackers slipped backdoors into the browser extension version 2.68 using leaked API keys from the source code.
It stole data on wallet unlocks, leading to $8.5 million in crypto losses. They rolled back to 2.69 and reimbursed users, but it underscored the registry and endpoint risks.
Even older cases like CircleCI’s 2023 incident fit the pattern. Malware on one engineer’s laptop stole SSO cookies, allowing attackers to scout and steal customer data for weeks.
SITF maps all this to its pillars, showing common threads like weak endpoint security leading to CI/CD chaos.
Why Old Frameworks Fall Short
We’ve got great resources out there, but they don’t fully cover SDLC threats. MITRE ATT&CK shines for spotting endpoint tricks, yet it skips the flow from a dev’s laptop to production pipelines.
OWASP’s CI/CD Top 10 flags the top risks nicely, but doesn’t show how an IDE slip can turn into a registry flood.
Others, like SLSA, focus on building integrity, or NIST on processes; they’re helpful pieces but miss the big picture of attacker paths across infrastructure.
SITF changes that. It’s built for “producers” teams making software, letting you model real movement and get step by step fixes. No fluff, just visuals and checklists tailored to your setup.
How to Use SITF Hands-On
It’s dead simple and fully open-source. Head to the GitHub Pages site or clone the repo from wiz-sec-public/SITF.
No installs, no signups, everything runs in your browser, client-side, so your data stays private.
Fire up visualizer.html to drag techniques onto a canvas and connect them.
As you build a flow, it automatically generates a defense matrix in CSV or PDF format for reports. Switch to techniques-library.html to browse attacks by pillar, like all CI/CD entry points, with risks and fixes attached.
Want to tweak it? Edit techniques.json and run a Python script to rebuild the HTML. Contribute back by pulling requests for new tricks, like runner abuses in Amazon Q or misconfigs from CodeBreach that nearly hit AWS broadly. It’s community driven, so it evolves with threats.
What This Means for Security Teams
For folks deep in cybersecurity like OSINT researchers or incident responders, SITF is a game-changer. It turns vague “supply chain” talk into concrete models.
Audit your pipelines: check for fork PR triggers, set up OIDC for workflows, add data loss prevention on laptops, and parse VCS logs for odd patterns.
where teams juggle GitHub, GitLab, or Azure, it works offline and adapts easily. Model your stack today, and you’re ready for the next Shai-Hulud variant.
Early chain breaks save headaches, prioritize endpoint EDR and VCS locks first.
As attacks grow, tools like this make defense proactive. No more chasing shadows. SITF hands you the map to fight back smarter.(Source)
Site: cybersecuritypath.com

%20(1).webp)

.webp)




