A surge in tech support scams on February 2, 2026, at approximately 16:00 UTC, affecting users across 48 U.S.-based organizations in sectors such as healthcare, manufacturing, and technology.
The campaign weaponizes malicious Bing Ads as the entry vector, leveraging innocuous search queries such as “Amazon” to funnel victims into a multi-stage redirect chain that culminates in scam pages hosted on Azure Blob Storage.
Attack Chain Breakdown
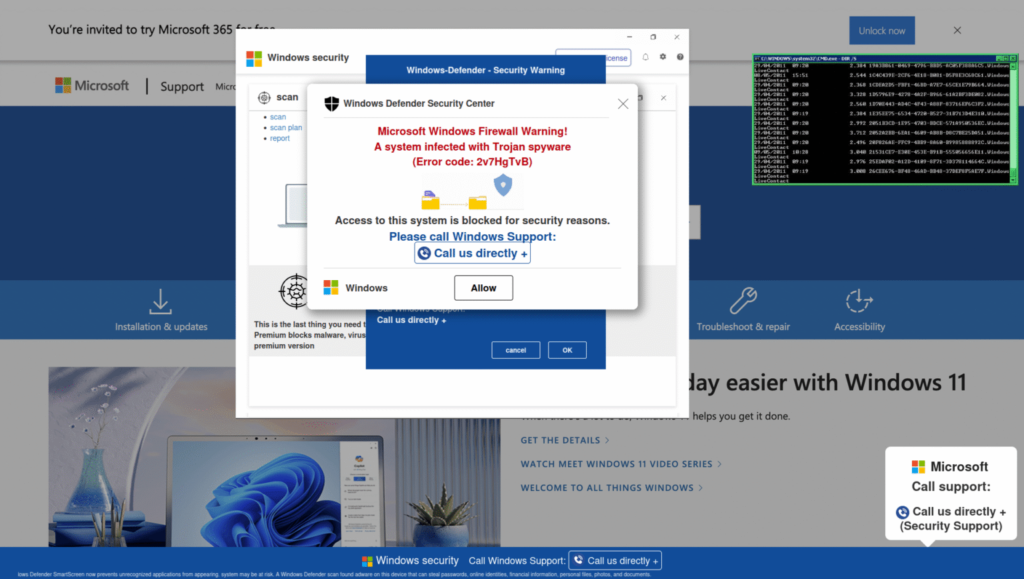
The infection begins with a poisoned ad in Bing search results, directing users to highswit[.]space, a domain registered via Namecheap on January 30, 2026, which runs an unserved WordPress instance with no visible content.
Server-side redirects (likely via 302 HTTP responses or JavaScript) propel victims to Azure Blob Storage endpoints.
This abuse exploits Azure’s blob.core.windows.net infrastructure, which permits public read access without authentication, making it ideal for ephemeral malicious hosting.
Scam pages mimic legitimate tech support portals, deploying HTML5/JavaScript overlays that display fake virus alerts, run system scans, and show persistent pop-ups urging users to call toll-free numbers.
Telemetry shows immediate execution upon load, with no exploits required, pure social engineering.
URL Patterns and IOCs
All malicious payloads adhere to this standardized pattern:
<container>.blob.core.windows.net/<random_string>/werrx01USAHTML/index.html?bcda=<phone_number>- <container>: Randomized alphanumeric strings (e.g., 2222wny78new832zzz), evading static blocklists.
- <random_string>: Variable folder (e.g., yyyyyyy), likely for segmentation.
- werrx01USAHTML/index.html: Fixed payload path, serving ~50KB HTML/JS scam kit.
- ?bcda=<phone_number>: Query parameter embedding U.S. toll-free numbers for victim callback.
Observed phone numbers:
- 1-866-520-2041
- 1-833-445-4045
- 1-855-369-0320
- 1-866-520-2173
- 1-833-445-3957
Over 70 unique Azure containers identified, including:
- 2222wny78new832zzz[.]blob[.]core[.]windows[.]net
- 22zz78new832zzzz[.]blob[.]core[.]windows[.]net
- nsjxsxsdxd788bnz89zz[.]blob[.]core[.]windows[.]net
- yy822ynew9983zzzz[.]blob[.]core[.]windows[.]net
(Full list available in Netskope’s advisory.)
Technical Implications and Mitigations
Attackers likely purchase Bing Ads using stolen credentials or through affiliate networks, bypassing Microsoft’s ad review by cloaking (benign landing pages for bots, redirects for users).
Azure containers evade takedown because of Microsoft’s decentralzed blob model:, public blobs persist until manually purged.
Defenses: Enforce direct navigation (e.g., bookmarks for amazon.com); deploy browser extensions like uBlock Origin for ad-blocking; monitor for blob.core.windows.net in proxy logs with YARA rules matching /werrx01USAHTML/.
This campaign highlights trends in cloud storage abuse, echoing prior incidents involving DigitalOcean and StackPath. Bing/Microsoft has not commented; block these IOCs immediately.
Site: cybersecuritypath.com

%20(1).webp)

.webp)




