.webp)
Keenadu Android Backdoor Infects Firmware Google Play RCA
A sophisticated Android backdoor that embeds itself deep into device firmware, compromising every app on infected tablets.
This malware, linked to major botnets such as Triada and BADBOX, spreads not only through tainted firmware builds but also through seemingly legitimate apps on Google Play.
Keenadu Android Backdoor Infect
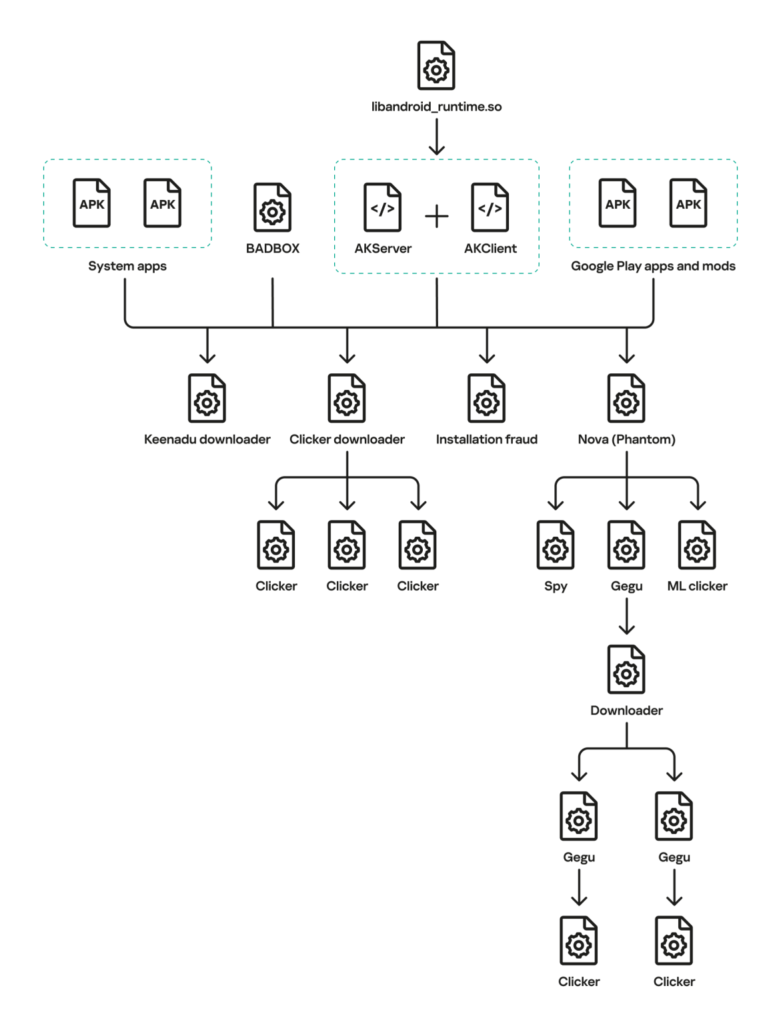
Keenadu infiltrates during firmware compilation, when attackers link a malicious static library, libVndxUtils.a, into the critical libandroid_runtime.so file located at /system/lib(64)/libandroid_runtime.so.
This library handles core logging functions like println_native for android.util.Log, but the tampered version calls a suspicious function that decrypts an RC4-encoded payload and loads it via DexClassLoader into the Dalvik cache.
The payload spawns AKServer in the privileged system_server process, forked from Zygote, and AKClient instances in all other apps, creating a client-server architecture on Android’s Binder IPC.
This sets up a bypass because the backdoor runs in every process’s address space. It uses protected broadcasts like com.action.
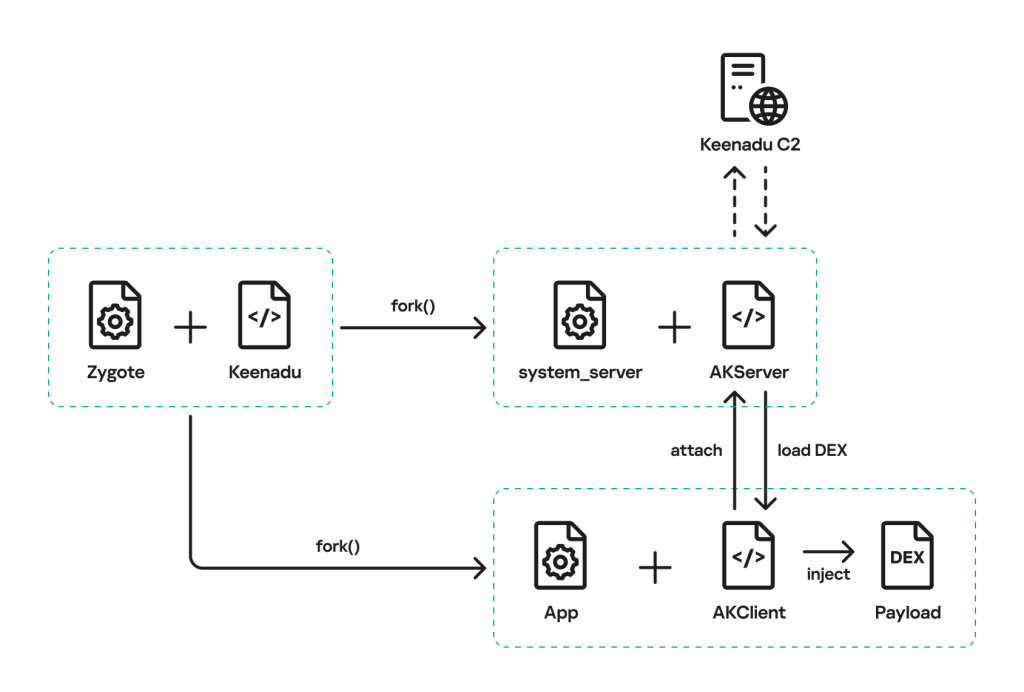
SystemOptimizeService to establish communication and enable remote DEX loading tailored to specific apps.
Firmware images, including those for Alldocube iPlay 50 mini Pro tablets from August 2023 onward, bear valid signatures, pointing to a supply chain compromise rather than post build tampering.
Google Play Connection
Beyond firmware, Keenadu modules appear in Google Play apps, such as smart camera software from com.taismart.global, which was downloaded over 300,000 times before its removal.
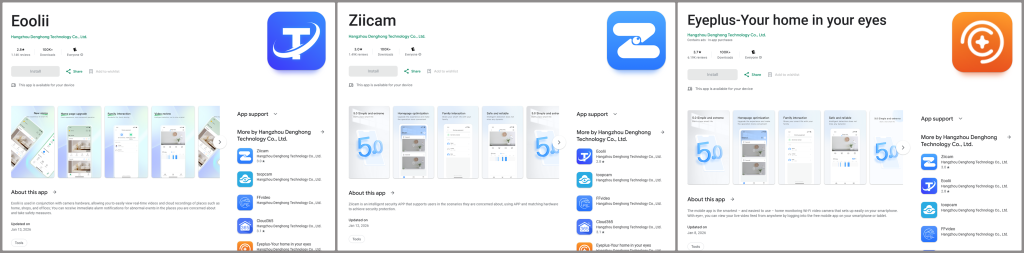
These apps embed services like com.arcsoft.closeli.service.KucopdInitService, which triggers loaders such as the Nova/Phantom clicker under specific conditions.
Kaspersky telemetry links this to firmware infections, where C2 servers push identical payloads.
One Play distributed payload retrieves Google Ads IDs via Settings.SGAID3 for tracking, while others hide in system apps like facial recognition services (com.aiworks.faceidservice).
Infected firmware sometimes delivers via OTA updates, blending legitimate channels with backdoor persistence.
Keenadu’s multi-stage loader fetches encrypted modules from AWS-hosted C2 servers after AES-128-CFB decryption (keys derived from MD5 hashes like ota.host.ba60d29da7fd4794b5c5f732916f7d5c).
Payloads use DSA signatures and MD5 checks before execution. They target apps like Chrome (com.android.chrome) to hijack URLbar searches, redirect queries, or monitor incognito mode; launchers for install monetisation via session-based APKs; and browsers/wallpapers for ad click fraud using ML and WebRTC.
C2 communication uses POST to /ak/api/pts/v4 with IMEI MD5 (‘m’) and network type (‘w’/’m’), skipping Chinese locales or Play less devices.
Keenadu connects to Triada (via shared C2 like zcnewy.com), BADBOX (matching Binder interfaces/IPC), and Vo1d, forming a web of prolific Android botnets. As of February 2026, it hit 13,715 devices, peaking in Russia, Japan, Germany, Brazil, and the Netherlands.
Attackers grant/revoke permissions remotely, geolocate, and exfiltrate data, though current ops focus on ad fraud. Remediation requires reflashing the firmware, as the system partition is read-only. Disable infected system apps via ADB where possible.
| Category | IoC / Indicator | Notes |
|---|---|---|
| Malicious Libraries | bccd56a6b6c9496ff1acd40628edd25e, c4c0e65a5c56038034555ec4a09d3a37, cb9f86c02f756fb9afdb2fe1ad0184ee | Malicious libandroid_runtime.so variants |
| Keenadu Payloads | 2922df6713f865c9cba3de1fe56849d7, 3dae1f297098fa9d9d4ee0335f0aeed3, 462a23bc22d06e5662d379b9011d89ff | Core malware payloads |
| Infected System Apps | 07546413bdcb0e28eadead4e2b0db59d, 0c1f61eeebc4176d533b4fc0a36b9d61, 10d8e8765adb1cbe485cb7d7f4df21e4 | Loader injection targets |
| Nova Clicker Apps | 0bc94bc4bc4d69705e4f08aaf0e976b3, 1276480838340dcbc699d1f32f30a5e9, 15fb99660dbd52d66f074eaa4cf1366d | Click-fraud modules |
| Payload CDN Domains | ubkt1x.oss-us-west-1.aliyuncs.com, m-file-us.oss-us-west-1.aliyuncs.com, pkg-czu.istaticfiles.com | Delivery of malware payloads |
| C2 Servers / Domains | 110.34.191.81, 110.34.191.82, 67.198.232.4, fbsimg.com, tmgstatic.com | Command and control infrastructure |
This threat underscores firmware supply-chain risks and evades Play Protect and app isolation. Vendors like Alldocube released infected updates after the acknowledgment, urging users to verify OTA sources.
Site: cybersecuritypath.com



