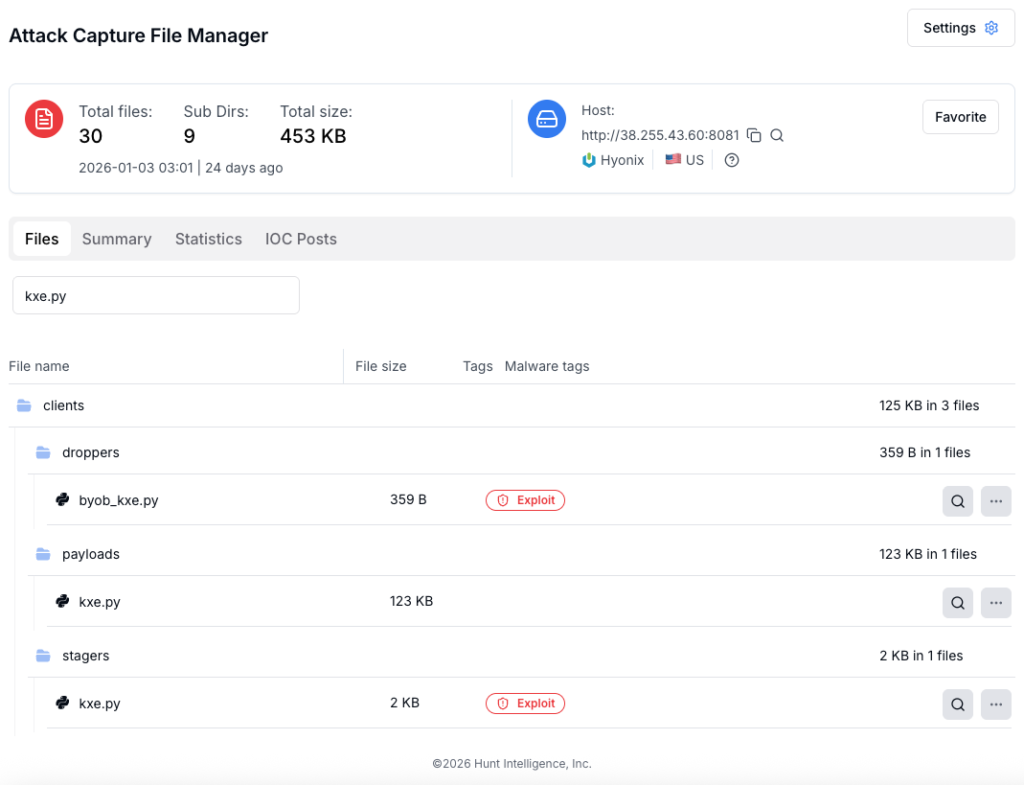
Threat hunters recently uncovered an exposed directory on a live command-and-control (C2) server hosting a complete Build Your Own Botnet (BYOB) framework deployment.
The server at IP 38.255.43.60:8081, hosted by Hyonix in the US, was serving droppers, stagers, payloads, and post-exploitation modules for cross-platform attack.
This modular Python-based RAT targets Windows, Linux, and macOS, with multi-stage infection chains, seven persistence methods, and capabilities such as keylogging, packet sniffing, and Outlook email theft.
Open directories on the attacker infrastructure often reveal active campaigns. Directory browsing via tools like Hunt.io’s AttackCapture captured the full structure: /droppers/, /clients/stagers/, /clients/payloads/, and modules for persistence, keylogging, processes, Outlook, packetsniffer, and escalation.
Analysis shows a three-stage chain designed to evade detection, with encrypted HTTP C2 on non-standard ports.
Infection Chain Breakdown
BYOB is a chain that keeps payloads small and conditional, fetching later stages only after checks pass.
- Stage 1: Dropper (byob_*.py, ~359 bytes)
- Ultra-compact Python loader with 4 layers of obfuscation: base64 decode → zlib decompress → marshal deserialize → exec in memory. It imports sys, zlib, base64, marshal, json, and urllib. These lines make it compatible with Python 2/3 (unified urlopen checks the version). Deobfuscated: it downloads the stager from hxxp://38.255.43.60:8081////clients/stagers/kxepy (see // for potential WAF bypass). No disk writes in-memory handoff only.
- Stage 2: Stager (kxe.py, ~2 KB)
- Adds anti-VM checks before payload fetch. Scans for “VIRTUALBOX” (VirtualBox indicator) and processes via tasklist (Windows) for virtualboxservice, virtualmachine toolsd, virtualmachine mem, etc. If detected, prompts “Virtual machine detected. Abort?” (often commented out). Fetches payload from hxxp://38.255.43.60:8081////clients/payloads/kxe.py, optionally decrypts with XTEA (Base64 key), then execs it.
- Stage 3: Payload (kxe.py, ~123 KB)
- Full RAT with sys. platform detection (‘win32’, ‘linux’, ‘darwin’), public IP via api.ipify.org, local IP via socket. gethostbyname, and more recon (MAC, arch, hostname, user, admin check, geolocation via ipinfo.io). Loads modules dynamically over encrypted HTTP C2. Persistence, keylogging, etc., activate post recon.
Core Post-Exploitation Capabilities
The payload’s modular design supports surveillance and control.
Persistence (7 Methods)
Cross-platform staying power:
- Windows: HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Java-Update-Manager (registry), %AppData%\Microsoft\Windows\Start Menu\Programs\Startup\Java-Update-Manager.eu.url (Startup folder .eu shortcut), scheduled tasks (hourly), WMI (__EventFilter + CommandLineEventConsumer).
- Linux: /etc/crontab entry.
- All: Hidden files (. prefix or attrib +h).
- macOS: ~/Library/LaunchAgents plist + /var/tmp script.
- Mimics “Java-Update-Manager” for disguise.
Keylogger
Platform hooks (pyHook on Windows, pyxhook on Unix): Logs keystrokes with window context ([Google Chrome]), handles backspace/delete for clean output, ignores non-printables. Buffers to StringIO, exfils via C2.
Process Control
Enumerates via tasklist/ps, kills by PID/name (taskkill /f or kill -9), searches keywords, monitors spawns, blocks AV (e.g., auto-kill taskmgr.exe).
Outlook Harvesting (Windows)
COM automation: pythoncom.CoInitialize, win32com.client.Dispatch(‘Outlook.Application’).GetNameSpace(‘MAPI’).GetDefaultFolder(6) for the inbox. Searches keywords in body/subject/sender, counts items, JSON exfil without creds (uses session).
Packet Sniffer
Raw sockets (admin/root needed): Parses IP headers (struct ‘!6H4s4s’ for version/IHL/TOS/len/ID/flags/TTL/proto/checksum/src/dst), logs like Wireshark, strips for TCP/UDP follow-on.
UAC Escalation
![Threat intelligence summary for 38[.]255[.]43[.]60](https://cybersecuritypath.com/wp-content/uploads/2026/01/image-6-1024x683.png)
Check IsUserAnAdmin() or getuid()==0. If not elevated, win32com.shell.shell.ShellExecuteEx(‘runas’, sys. executable, script + ‘ asadmin’) triggers a consent prompt disguised as a Java update.
C2 -AES-256-CBC over HTTP (8080-8083), module delivery – exfil to 8083.
Infrastructure Details
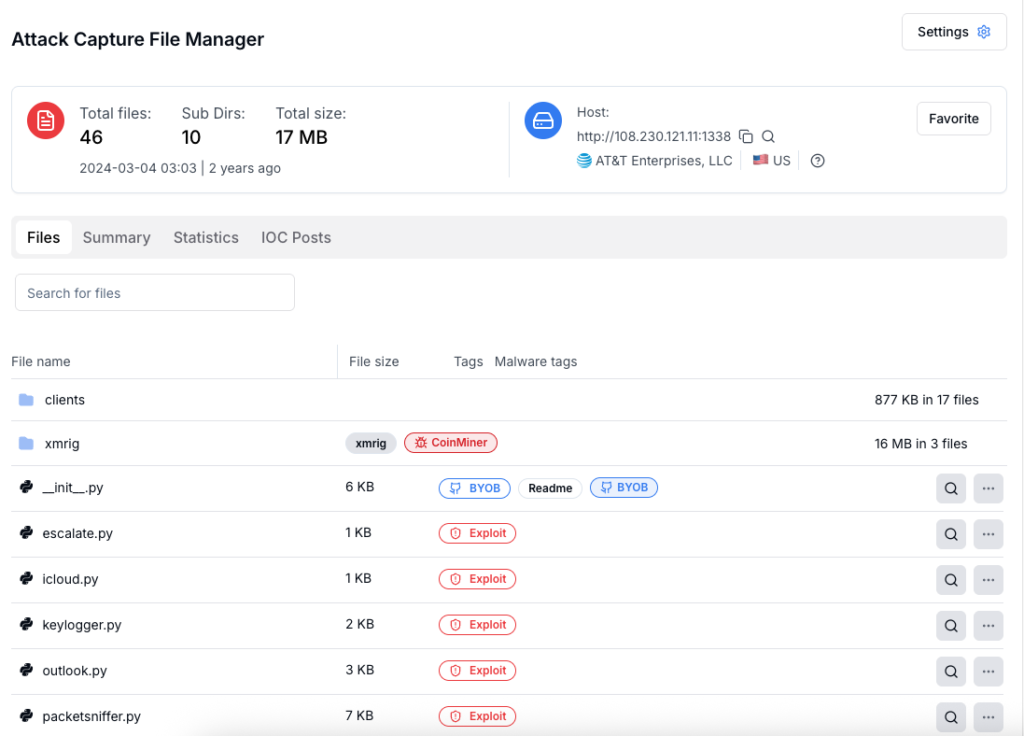
From dropper paths, a total of 5 active nodes (US, Singapore, Panama) have been estimated over ~10 months (Mar 2024 – Jan 2026). Hyonix US Node (38.255.43.60) is IIS/Apache/PythonHTTP and RDP: 3389. Two nodes dual-host XMRig miners. Discovery via filename “/droppers/byob_” searches.
| Type | Indicator | Description |
|---|---|---|
| IP | 38.255.43.60 | Primary C2 (Hyonix, US, port 8081) |
| IP | 15.235.186.150 | Singapore node (BYOB + XMRig) |
| IP | 108.230.121.11 | US AT&T node (BYOB + XMRig, port 1338) |
| Port | 8081/TCP | Payload distro (Python SimpleHTTP) |
| Port | 8080/TCP, 8082/TCP, 8083/TCP | C2/modules/exfil |
| Registry | HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Java-Update-Manager | Windows persistence |
| File | %AppData%\Microsoft\Windows\Start Menu\Programs\Startup\Java-Update-Manager.eu.url | Windows Startup |
| Task | Java-Update-Manager (hourly) | Windows scheduled task |
| WMI | __EventFilter: Java-Update-Manager | Windows WMI persistence |
| File (Linux) | /etc/crontab (malicious entry) | Linux crontab |
| File (macOS) | ~/Library/LaunchAgents/com.apple.update.manager.plist | macOS LaunchAgent |
| MD5 | 76e8ff3524822f9b697af1b7f9a96712 | byob_kxe.py (dropper) |
| MD5 | 5c61a8720aa0b9a28973be3f0eedf042 | kxe.py (stager) |
| MD5 | 72caa7b8bb22c80a2bc77c17d1a35046 | kxe.py (payload) |
| MD5 | cd06fc1d25a5636a7e953c672e1fa3ba | keylogger.py |
MITRE ATT&CK Highlights: T1059.006 (Python), T1547.001 (Run Keys), T1056.001 (Keylog), T1114.001 (Email Collection), T1040 (Sniffing), T1071.001 (HTTP C2).
Detection and Response
Network: Watch HTTP to 8080-8083, Python procs to ipify/ipinfo, paths with ////clients/.
Endpoint: New Python-linked Run keys/.eu.url/tasks/WMI, pyHook hooks, Outlook COM from non-Outlook, raw sockets.
Mitigate: Allowlist Python, log PowerShell/WMI/Sysmon, block high ports, train on UAC fakes.
IRISOLATE, memdump on them, nuke persistence, and look through logs for LOMPs.
This leak demonstrates BYOB’s maturity as an all-in-one RAT tool and its ability to incorporate evasion, persistence, and broad post-comp capabilities. Infra rotation and mining side-hustle suggest ops for days.(source: Hunt)
site: cybersecuritypath.com

%20(1).webp)

.webp)




