BeyondTrust’s remote support software is under active exploitation via CVE-2026-1731, a critical pre-authentication remote code execution flaw. Attackers deploy VShell and SparkRAT backdoors post-compromise, targeting sectors like finance and healthcare across multiple countries.
CVE-2026-1731 strikes the thin-scc-wrapper component, which manages WebSocket connections in BeyondTrust Remote Support and Privileged Remote Access. Authenticated attackers craft a malicious remoteVersion value during the handshake, exploiting bash arithmetic evaluation to inject commands such as $(cmd), which execute as the site user.
This OS command injection (CWE-78) carries a CVSS v4 score of 9.9 due to its network reach, low complexity, and severe impact on confidentiality and integrity. BeyondTrust patched it via advisory BT26-02 on February 6, 2026, urging self-hosted users to upgrade Remote Support to 25.3.2 or Privileged Remote Access to 25.1.1.
CISA added it to the Known Exploited Vulnerabilities catalog on February 13, mandating federal fixes and flagging it for private entities. Cortex Xpanse detected over 16,400 exposed instances, many of which are unpatched on-premises setups.
Track active exploitation of CVE-2026-1731 as of late February 2026, with confirmed compromises enabling webshells, backdoors, and data theft. No major scope expansions reported since February 19.
Observed Post-Exploitation Tactics
Attackers leverage RCE for these activities:
- Domain/local admin account creation and recon on trusts/admins.
- Backdoor deployment (SparkRAT, VShell).
- Remote tools (SimpleHelp, AnyDesk) and tunnels (Cloudflare, ligolo-ng).
- Webshell installs (PHP eval, aws.php, bash droppers with config stomping).
- Data exfiltration (PostgreSQL dumps, configs).
Exploitation surged post-PoC on February 10; GreyNoise noted probes by Feb
VShell, SparkRAT Exploit BeyondTrust
Exploitation starts with WebSocket probes to /nw paths or get_portal_info endpoints. The payload, such as a[$(id)]0, evades partial sanitization and runs shell commands without login.
Post-RCE, attackers escalate via custom Python scripts that hijack admin User ID 1 for 60 seconds by swapping database password hashes, then self-delete. They deploy one-line PHP webshells (e.g., eval via POST[‘1’]) and multi-vector ones like aws.php, which Base64-decode ‘ASS’ payloads with CRLF delimiters akin to China Chopper.
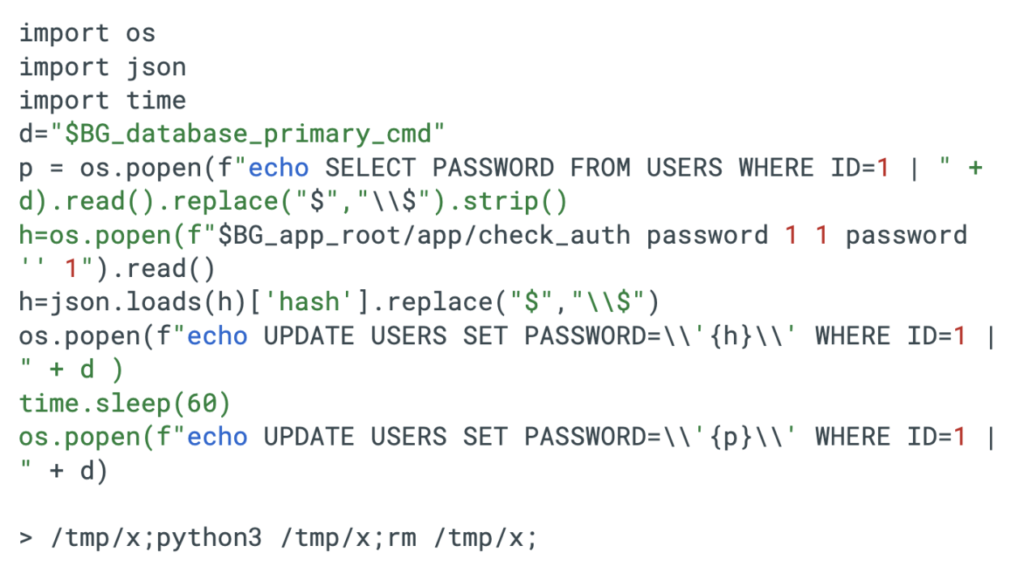
Bash droppers use config stomping: they plant file_save.php and tweak Apache configs in memory to route to ns/tmp/php-fpm. sock, restart the service, and restore clean files to dodge forensics.
SparkRAT, a Go-based cross-platform RAT from 2022 campaigns like DragonSpark, appeared widely (hash: 9f431d5549a03aee92cfd2bdbbe90f1c91e965c99e90a0c9ad5a001f4e80c350). It enables persistent C2 over URLs like 138.197.14[.]95/ws.
VShell, a fileless Linux backdoor (hash: 98a7b0900a9072bb40af579ec372da7b27af12b15868394df51fefe290ab176b), masquerades as legit services for stealthy access via aliyundunupdate[.]xyz:8084/slt. Attackers also push SimpleHelp, AnyDesk, Nezha agents, and ligolo-ng tunnels.
Download cradles chain wget/curl/python for blue.drx scripts from transfer.weepee[.]io. Reverse shells hit Metasploit-like ports (e.g., 144.172.103[.]200:4444). DNS tunneling via oastify[.]com nslookups exfils hostnames in hex chunks, evading firewalls.
Compromises in U.S., France, Germany, Australia, and Canada financial, legal, tech, education, retail, and healthcare firms. Recon includes domain admin scans, persistence via new accounts, and lateral moves with tools like Cloudflare tunnels.
Data theft chains tar PostgreSQL dumps and configs for C2 exfil. This echoes CVE-2024-12356, exploited by Silk Typhoon for U.S. Treasury breaches, highlighting recurrent WebSocket validation gaps.
| CVE ID | CVSS Score | Type | Affected Products | Disclosure Date |
|---|---|---|---|---|
| CVE-2026-1731 | 9.9 (v4) | OS Command Injection (CWE-78) | Remote Support (RS), Privileged Remote Access (PRA) older versions | Feb 6, 2026 |
| CVE-2024-12356 | 9.8 (v3.1) | Command Injection | PRA, RS up to 24.3.1 | Dec 2024 |
Palo Alto Networks provides layered protection against CVE-2026-1731 exploitation and post-compromise activity through its security portfolio. These focus on prevention, detection, exposure management, and response.
Windows flags bomgar-scc.exe spawning cmd/powershell with net domain or vssadmin (risk scores to “Critical”); Linux spots bomgar-scc curling whoami or useradd.
Patch immediately; segment remote access behind zero-trust gateways. Palo Alto tools like Cortex XDR block post-exploitation, Advanced URL Filtering tags C2 domains, and Xpanse alerts on exposures.
| Category | Indicator |
|---|---|
| IP | 23.162.40[.]187 |
| IP | 37.19.221[.]180 |
| IP | 45.61.150[.]96 |
| IP | 70.23.0[.]66 |
| IP | 82.29.53[.]187 |
| IP | 82.29.72[.]16 |
| IP | 83.138.53[.]139 |
| IP | 85.155.186[.]121 |
| IP | 92.223.44[.]134 |
| IP | 98.10.233[.]76 |
| IP | 134.122.13[.]34 |
| IP | 138.197.14[.]95 |
| IP | 142.111.152[.]50 |
| IP | 144.172.103[.]200:4444 |
| IP | 155.2.215[.]64 |
| IP | 178.128.212[.]209 |
| IP | 179.43.146[.]42 |
| URL | 138.197.14[.]95/ws (SparkRAT) |
| URL | hxxp[:]//64.31.28[.]221/support |
| URL | aliyundunupdate[.]xyz:8084/slt (VShell) |
| URL | d65sb7ngveucv5k2nm508abdsjmbn7qmn.oast[.]pro |
| URL | q0r2e5q2dzbykcox9qmkptm12s8mwb.oastify[.]com |
| URL | hxxp[:]//134.122.13[.]34:8979/c (SparkRAT) |
| URL | hxxp[:]//82.29.53[.]187:8778/app_cli |
| URL | hxxps[:]//transfer.weepee[.]io/7nZw7/blue.drx |
| URL | hxxp[:]//85.155.186[.]121/access (SimpleHelp) |
| URL | hxxps[:]//temp[.]sh/tQTSs/storm.exe |
| URL | hxxps[:]//64.95.10[.]115:23011/update.sh |
| URL | hxxps[:]//judiemkqjajsfzpidfjlowgl8nyrtd49x.oast[.]fun |
| URL | hxxps[:]//raw.githubusercontent[.]com/nezhahq/scripts/main/agent/install.ps1 |
| Hash | 9f431d5549a03aee92cfd2bdbbe90f1c91e965c99e90a0c9ad5a001f4e80c350 (SparkRAT) |
| Hash | 98a7b0900a9072bb40af579ec372da7b27af12b15868394df51fefe290ab176b (VShell) |
| Hash | 66cceb2c2f1d9988b501832fd3b559775982e2fce4ab38fc4ffe71b74eafc726 (maintenance.php) |
| Hash | 679ee05d92a858b6fe70aeb6072eb804548f1732e18b6c181af122b833386afb (d6) |
| Hash | 4762e944a0ce1f9aef243e11538f84f16b6f36560ed6e32dfd9a5f99e17e8e50 (SimpleHelp Installer) |
| Hash | 98442387d466f27357d727b3706037a4df12a78602b93df973b063462a677761 (aws.php) |
| Hash | cc2bc3750cc5125a50466f66ae4f2bedf1cac0e43477a78ed2fd88f3e987a292 (Bash Script) |
| Hash | cf83e1357eefb8bdf1542850d66d8007d620e4050b5715dc83f4a921d36ce9ce (file_save.php) |
| Hash | 0ecc867ce916d01640d76ec03de24d1d23585eb582e9c48a0364c62a590548ac |
Site: cybersecuritypath.com
Reference: Source

%20(1).webp)

.webp)




